Agent
Agent configuration for Crow CI workers.
Minimum Configuration
Section titled “Minimum Configuration”CROW_SERVER=crow-server:9000CROW_AGENT_SECRET=<token>| Variable | Description |
|---|---|
CROW_SERVER | Server gRPC address (no protocol prefix) |
CROW_AGENT_SECRET | Authentication token from server |
Parallel Workflows
Section titled “Parallel Workflows”CROW_MAX_WORKFLOWS=4By default, agents execute one workflow at a time. Increase based on available resources.
Workflow Filtering
Section titled “Workflow Filtering”Crow routes workflows to agents using two mechanisms:
| Method | Description |
|---|---|
| Labels | Filter by matching key-value pairs |
| Priority | Prefer agents with higher priority when multiple match |
Labels
Section titled “Labels”Agents have built-in labels:
| Label | Description |
|---|---|
backend | Execution backend (docker, kubernetes, local) |
type | Agent type |
platform | OS/architecture |
agent | Agent identifier |
Add custom labels to route specific workflows:
# Agent configurationCROW_AGENT_LABELS='gpu=true,memory=high'# Workflow configuration (.crow.yaml)labels: gpu: true memory: highOnly agents with matching labels will process workflows with those labels.
Priority
Section titled “Priority”When multiple agents match, higher priority agents are preferred:
CROW_AGENT_PRIORITY=100Use this to prefer agents with more capacity when available.
Agent Types
Section titled “Agent Types”Global Agents
Section titled “Global Agents”Admin-managed agents that process all workflows. Configure via environment variables on the agent.
Organization/User Agents
Section titled “Organization/User Agents”Non-admin users can register agents scoped to their org or user account.
Remote agent configuration:
CROW_GRPC_ADDR=crow.example.com:9000CROW_GRPC_SECURE=trueCROW_AGENT_SECRET=<token>CROW_BACKEND=dockerMulti-Org Agents
Section titled “Multi-Org Agents”Process workflows from multiple specified organizations or repositories.
# Multiple orgs (pipe-separated)CROW_CUSTOM_LABELS='org=1|2|3'
# Alternative syntax (comma-separated, merged internally)CROW_CUSTOM_LABELS='org=1,org=2,org=3'
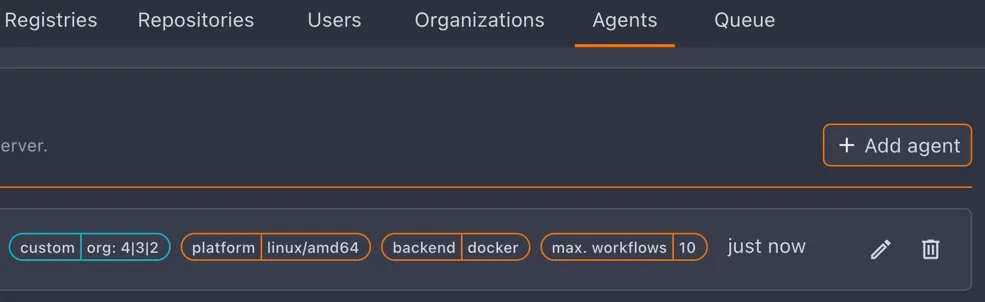
# Limit to specific reposCROW_CUSTOM_LABELS='org=myorg,repo=myorg/specific-repo'Multi-org labels appear highlighted in the agent list:
Backend Options
Section titled “Backend Options”Configure backend-specific settings at the agent level. See environment variables for all CROW_BACKEND_* options.
Local Backend Sandboxing
Section titled “Local Backend Sandboxing”Enable process isolation using macOS sandbox-exec:
CROW_BACKEND_LOCAL_SANDBOX_LEVEL=standard| Level | Network | System Access | Use Case |
|---|---|---|---|
none | ✅ Full | ✅ Full | Trusted code only |
standard | ✅ Full | ⚠️ Limited | Most CI/CD workloads |
strict | ❌ Blocked | ❌ Minimal | Offline builds, maximum isolation |
Standard level details:
| Allows | Denies |
|---|---|
| Network access (npm, go get, pip) | Writing outside workflow dirs |
| System libraries and frameworks | Sensitive user dirs (Documents, Desktop) |
| Shell configs (.bashrc, .zshrc) | SSH private keys |
| Workflow temp directories |
none runs processes without isolation. Only use with fully trusted code.